News

DJI's Efforts to Distance Themselves from Chinese Ownership and Ensure Data Security In recent years, DJI, the world's leading drone manufacturer, has faced increasing scrutiny over its Chinese ownership and concerns about data security. In response, DJI has taken several significant steps to address these concerns and reassure users that their data is secure. Distancing from Chinese Ownership One of the most notable efforts by DJI to distance itself from Chinese ownership is the establishment of Anzu Robotics, a Texas-based startup. Anzu Robotics claims to have no business relationship with DJI, yet it sells drones that bear remarkable similarities to DJI's products. This move was seen as an attempt to bypass the impending U.S. ban on Chinese drones. However, Anzu Robotics has since stated that it has no business relationship with DJI, following an investigation by the U.S. House Select Committee on the Chinese Communist Party. Ensuring Data Security DJI has implemented a range of measures to enhance data security and privacy for its users. These measures include: 1 . Trusted Execution Environment (TEE) : DJI employs TEE and FIPS-certified DJI Core Crypto Engine for strong chip and hardware security. a. Isolation : The TEE creates a secure environment that isolates critical security functions from the main operating system. This isolation helps protect sensitive data and cryptographic operations from being tampered with or accessed by unauthorized parties. b. Secure Boot : The TEE ensures that the drone's firmware and software are securely booted, preventing unauthorized modifications or malicious software from compromising the system. c. Data Protection : By using the TEE, DJI ensures that sensitive data, such as flight logs and user information, is stored and processed securely. This helps prevent data breaches and unauthorized access to personal information. . d. Cryptographic Operations : The TEE supports cryptographic operations, such as encryption and decryption, using the FIPS-certified DJI Core Crypto Engine. This ensures that data is encrypted and decrypted securely, providing robust protection against potential attacks. e. Hardware Security : The TEE is implemented at the hardware level, making it resistant to software attacks and providing a secure foundation for the drone's security architecture. f. Data Encryption: Drone data shared with DJI is TLS-protected, and personal data is further secured with AES-256 encryption in storage. 2. Independent Security Audits: Since 2017, DJI has conducted regular independent security audits to validate its data security practices. These audits have consistently affirmed DJI's alignment with industry best practices. DJI has been proactive in ensuring the security of its products through regular independent security audits. Since 2017, DJI has engaged multiple federal agencies and private sector firms to validate its data security practices. Here are some key audits: a. FTI Consulting Audit (2024) : This audit assessed the DJI Mavic 3T, Pilot 2, and RC Pro, reaffirming that when U.S. operators choose to share flight data with DJI, the data resides within U.S.-based servers. It also validated that Local Data Mode (LDM) resulted in no outbound traffic. b. TÜV SÜD Audit (2022) : TÜV SÜD conducted an audit of DJI consumer drones (Air 2S, Mini 2, Mavic 3) and the DJI Fly app, confirming compliance with NIST IR 8259 and ETSI EN 303645 standards for network security and privacy protection. c. Booz Allen Hamilton Audit (2020) : This audit focused on DJI commercial drone products (Mavic Pro GE, Matrice 600 Pro GE, Mavic 2 Enterprise) and validated DJI's adherence to industry best practices. d. ISO 27001 Certification (2023) : DJI FlightHub 2 obtained ISO 27001 certification from the British Standards Institution (BSI), ensuring compliance with information security management standards. e. FIPS 140-2 Certification (2022) : The DJI Core Crypto Engine received NIST FIPS 140-2 certification, validating its security standards in design and implementation. f. These audits provide independent validation of DJI's robust data privacy practices and reinforce the company's commitment to maintaining high security standards. 3. Bug Bounty Program : DJI was the first drone maker to introduce a Bug Bounty Program, encouraging security researchers to detect and report potential vulnerabilities. 4. Local Data Mode (LDM) : This mode ensures that no outbound traffic occurs when U.S. operators choose to share flight data with DJI. Local Data Mode is a privacy feature introduced by DJI to give users more control over their data. When activated, LDM disables internet connectivity for the DJI app, preventing any data from being sent to or received from DJI or third-party servers4. Here are some key details: a. Functionality : LDM acts as a "kill switch" that blocks all outbound traffic from the DJI app, ensuring that no flight data is transmitted over the internet. b. Data Security : Independent audits by FTI Consulting confirmed that LDM effectively blocks all data transfers, except for map data when the "Map Request" feature is enabled. c. User Control : Users can choose to enable LDM to ensure that their data remains on their device, providing an additional layer of security for sensitive operations. d. Availability : LDM is available in the DJI Pilot app and has been expanded to other DJI apps, including DJI GO4 and DJI Fly. e. By implementing Local Data Mode, DJI empowers users to manage their data privacy and provides assurance that their flight data remains secure. DJI's commitment to data security and privacy is evident in its ongoing efforts to enhance privacy controls and engage with the drone community to strengthen its systems. By implementing these measures, DJI aims to build trust with its users and ensure that their data remains secure. In conclusion, DJI's efforts to distance itself from Chinese ownership and ensure data security demonstrate its commitment to addressing user concerns and maintaining a high standard of data protection. As the company continues to innovate and expand its product offerings, it remains dedicated to providing a secure and reliable experience for its customers.

Navigating the Skies: In-House Aerial Drone Service Versus UsingEstablished Providers In the ever-evolving landscape of aerial drone technology, organizations face a pivotal decision: Should they invest in creating an in-house aerial drone service or lean on the expertise of established drone service providers? The answer isn't always clear-cut and involves weighing numerous factors, from cost considerations to operational capabilities. In-House Aerial Drone Service: The Journey of Independence Embarking on the path to develop an in-house aerial drone service entails significant commitment and investment. Here are the core challenges to consider: 1. Initial Investment and Operational Costs: Establishing an in-house service requires substantial upfront capital for acquiring high-quality drones, supporting technology, and hiring skilled personnel. Beyond this, ongoing maintenance, training, and regulatory compliance contribute to sustained operational costs. 2. Technical Expertise and Training: Building a proficient drone team in-house means investing in continuous training and development to keep pace with rapidly advancing technology. This also includes staying updated with regulations and ensuring compliance. 3. Customization and Control: While an in-house service offers the advantage of tailored operations to meet specific needs, it demands meticulous planning and resources to design, implement, and manage these custom solutions. 4. Operational Scalability: Scaling an in-house service to accommodate growing or fluctuating demand can be challenging. Organizations must balance resource allocation with the ability to expand operations without compromising quality. Leveraging Established Drone Service Providers: The Road to Efficiency On the other hand, utilizing an established drone service provider can streamline operations and drive cost efficiency. Key considerations include: 1. Cost Efficiency: Providers dedicated to drone services often benefit from economies of scale, enabling them to offer competitive pricing. Outsourcing can reduce the burden of initial investments and ongoing operational costs. 2. Expertise and Experience: Established providers bring a wealth of experience and technical expertise, ensuring high-quality service delivery and the ability to handle complex operations with ease. 3. Access to Advanced Technology: Partnering with a reputable provider means access to the latest drone technology and innovations without the need for continual in-house investment. 4. Regulatory Compliance and Risk Management: Providers are well-versed in navigating the intricate landscape of regulations, ensuring compliance and mitigating potential risks associated with drone operations. 5. Focus on Core Competencies: Outsourcing allows organizations to concentrate on their core business activities, leaving the specialized drone operations to experts who can deliver efficient and reliable service. The Verdict Ultimately, the decision to develop an in-house aerial drone service or partner with an established provider hinges on an organization's unique needs, resources, and strategic goals. While an in-house service offers customization and control, it demands significant investment and ongoing commitment. Conversely, leveraging an established provider can enhance efficiency and cost-effectiveness, allowing organizations to focus on their core competencies. Careful consideration of these factors will help chart the best course for navigating the skies of aerial drone technology.
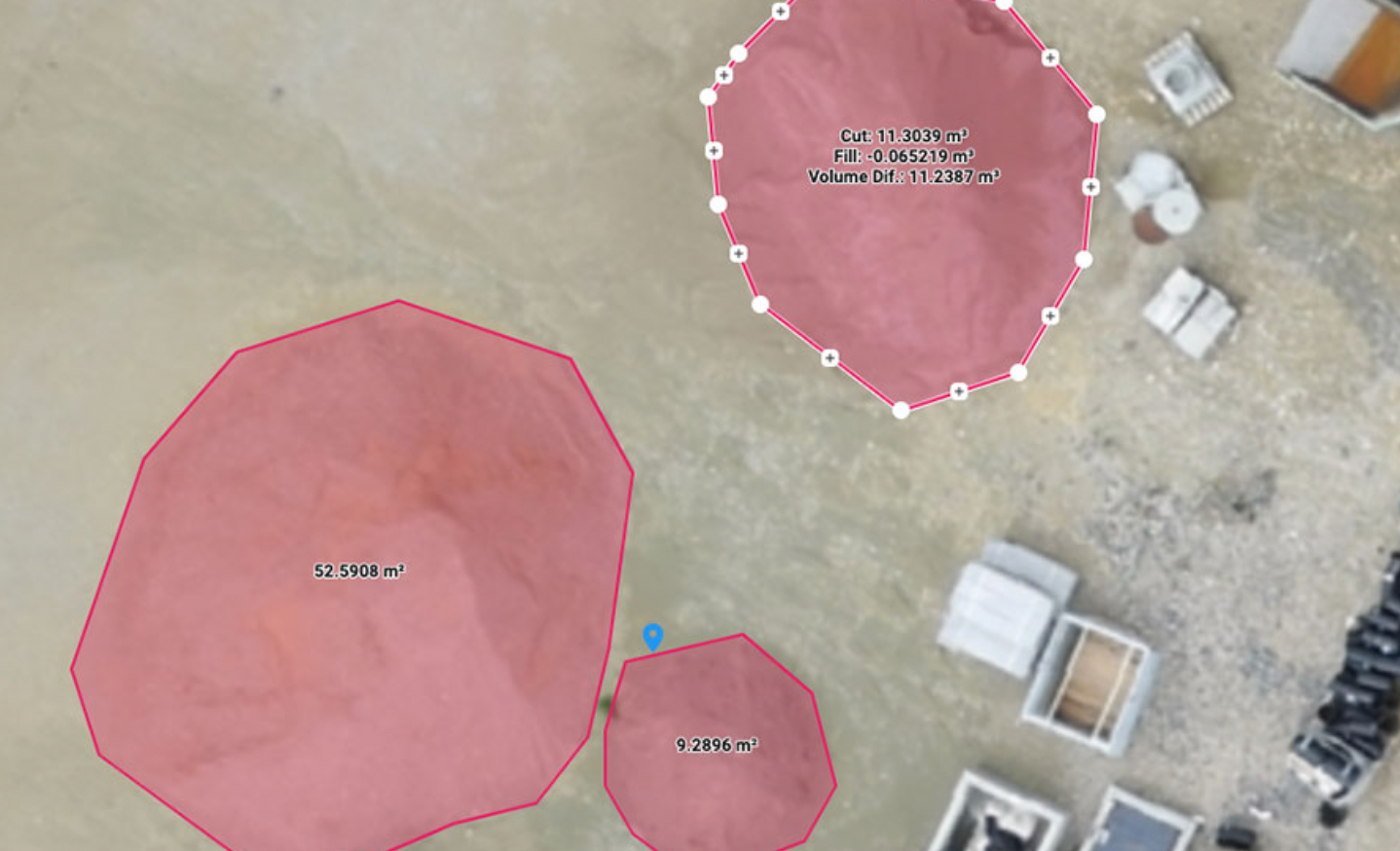
Unlocking the Benefits of Pix4D Cloud: Revolutionizing Aerial Imaging and More In today’s fast-paced industries, leveraging cutting-edge technology to improve efficiency and precision has never been more crucial. Pix4D Cloud is a powerful platform that empowers professionals to harness the full potential of aerial imaging for tasks such as volume analysis, construction progress tracking, and inspections. Here, we’ll explore the key benefits and value Pix4D Cloud brings to various sectors. 1. Streamlined Aerial Imaging Workflows Pix4D Cloud simplifies aerial imaging by providing a centralized, web-based platform for processing and managing drone-captured data. Users can upload images directly to the cloud, where advanced photogrammetry algorithms generate high-resolution 2D maps, 3D models, and orthomosaics. Why it matters: This eliminates the need for expensive hardware or software installations, allowing teams to access their data anytime, anywhere. With its user-friendly interface, Pix4D Cloud reduces the learning curve, making it accessible to both experienced professionals and newcomers. 2. Accurate Volume Analysis One of Pix4D Cloud’s standout features is its robust volume measurement capabilities. Whether calculating stockpile volumes in mining operations or assessing material quantities on construction sites, the platform provides precise and reliable results. Key benefits: - Automated volume calculations based on high-resolution 3D models. - The ability to compare data over time for tracking changes or discrepancies. - Significant time savings compared to traditional surveying methods. 3. Construction Progress Monitoring Construction projects demand meticulous planning and execution, often involving multiple stakeholders. Pix4D Cloud enables teams to document and monitor site progress with unparalleled accuracy. How it helps: - Regular drone flights can be used to create updated maps and models, providing visual and measurable records of progress. - Stakeholders can access real-time updates and reports from anywhere, fostering transparency and collaboration. - Early detection of potential issues helps mitigate delays and cost overruns. 4. Enhanced Inspections For industries like infrastructure, energy, and agriculture, inspections are critical for safety and performance. Pix4D Cloud optimizes inspection workflows with high-quality imagery and powerful analytical tools. Advantages include: - Safe, remote inspections of hard-to-reach or hazardous areas, reducing risk to personnel. - Detailed, shareable reports with annotations and measurements. - Rapid turnaround times, enabling faster decision-making and maintenance scheduling. 5. Cost-Effective and Scalable Pix4D Cloud is designed to grow with your business needs. Its pay-as-you-go model ensures affordability while delivering enterprise-level performance. By eliminating the need for on-site processing infrastructure, the platform reduces operational costs and supports scalability as your projects expand. 6. Collaboration and Accessibility Sharing data and insights with team members, clients, and stakeholders is seamless on Pix4D Cloud. The platform’s collaboration tools allow multiple users to review and comment on projects, streamlining communication and decision-making. What this means: Everyone involved in a project has access to the same accurate, up-to-date information, leading to improved alignment and efficiency. Conclusion Pix4D Cloud stands out as a transformative tool for professionals across industries. Its ability to deliver precise data, streamline workflows, and enhance collaboration makes it an invaluable asset for aerial imaging, volume analysis, construction progress tracking, and inspections. By adopting Pix4D Cloud, businesses can not only save time and resources but also achieve a higher standard of accuracy and performance in their operations. Ready to elevate your workflows? Explore the possibilities with Drone Logic and Pix4D and see the difference it can make for your projects.

Unlocking Value and Cost Savings with Aerial Drones for Photogrammetry In recent years, the use of aerial drones for photogrammetry has revolutionized various industries, offering unprecedented value and cost savings. By leveraging advanced drone technology, businesses can achieve high-precision mapping and 3D modeling at a fraction of the cost of traditional methods. Enhanced Efficiency and Speed Aerial drones can cover large areas quickly, significantly reducing the time required for data collection. This efficiency translates to faster project completion and the ability to handle multiple projects simultaneously. Cost-Effective Data Collection Traditional aerial photogrammetry often involves expensive aircraft and extensive crew. Drones, on the other hand, are relatively inexpensive to operate and maintain. This cost-effectiveness makes aerial photogrammetry accessible to a wider range of businesses, from small startups to large corporations. For example, a study found that using drones for surveying can reduce costs by up to 60% compared to traditional methods. Improved Data Quality and Resolution Modern drones are equipped with high-resolution cameras and advanced sensors, capturing detailed and accurate data. This high-quality data is crucial for applications such as urban planning, agriculture, and environmental monitoring, where precision is paramount. Reduced Environmental Impact Using drones for aerial photogrammetry minimizes the environmental footprint compared to traditional methods. Drones produce fewer emissions and require less ground disturbance, making them a more sustainable option for data collection. Versatility Across Industries From construction and mining to agriculture and disaster response, drones offer versatile solutions for various industries. Their ability to access difficult-to-reach areas and provide real-time data enhances decision-making and operational efficiency. Case Studies and Success Stories Numerous case studies highlight the value and cost savings associated with drone photogrammetry. For instance, construction companies have used drones to monitor project progress and detect potential issues early, saving time and money. Agricultural businesses have utilized drones for crop monitoring and yield prediction, optimizing resource allocation and increasing profitability. In one case, a construction company reported a 30% reduction in project costs by using drones for site surveys and progress monitoring. In conclusion, the integration of aerial drones into photogrammetry workflows presents a game-changing opportunity for businesses to achieve greater value and cost savings. By embracing this innovative technology, companies can enhance their operational efficiency, improve data quality, and contribute to a more sustainable future.
